
What do World War II fighter planes, a data sampling logic error known as survivorship bias, and modern data security have in common? More than you think.
In 1943, behind the doors of a nondescript Manhattan office building on the campus of Columbia University, sat some of the greatest mathematical minds of the day. Heads bent over desks and slide rules, the men and women of the Statistical Research Group (SRG) at Columbia University worked tirelessly to provide statistical and mathematical solutions to the latest military challenges, like the optimal mix of ammunition in aircraft machine guns or how best to improve the trajectory of missiles and torpedoes by calculating pursuit curves. Among the many brains at SRG (and there were several who would eventually become world famous in their fields), was Abraham Wald, founder of the field of statistical sequential analysis.
In recent years, Abraham Wald has become something of an internet celebrity for how he tackled the issue of improving the safety and security of WWII fighter planes and how the solutions relate to something called “survivorship bias.”
During WWII, as planes returned from missions, Wald discovered that engineers focused their reinforcement of a plane’s fuselage and engine based on data from the areas of the plane that sustained the most damage (i.e., bullet holes). Wald pointed out that by only studying the data from the returning planes, and ignoring the planes that did not return, engineers were likely engaging in survivorship bias; that is, data from hits on planes not returning from combat missions better demonstrated the crucial and most sensitive areas that most required reinforcement, not the other way around.
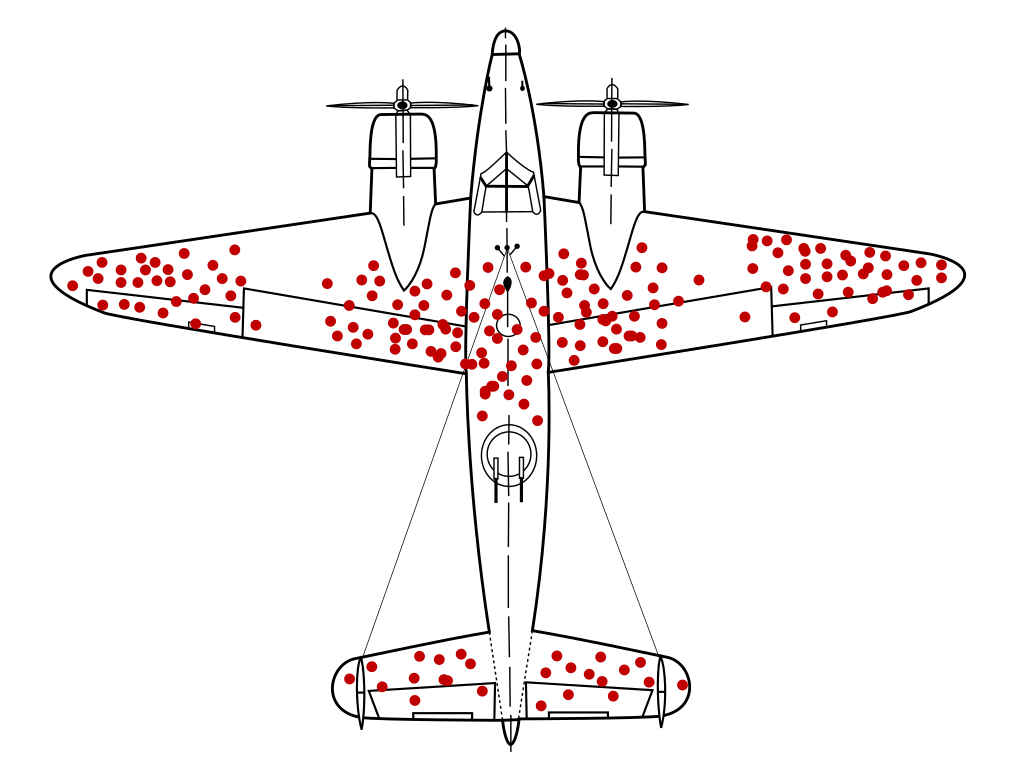

Source: Wikipedia
In the above figure (created in 2005 and based on a 1943 report by Abraham Wald), the damage pattern shows the hypothetical locations where a WWII plane could sustain damage and still return to base. Reinforcing the most commonly hit areas demonstrates survivorship bias because the data from the planes that didn’t return home was being ignored; presumably the fatally damaged planes were hit in other places resulting in non-survivability.
Are Cybersecurity Professionals Guilty of Survivorship Bias?
Survivorship bias is a logic error in which data sampling research focuses on entities that survive instead of those that do not, ultimately leading to mistaken conclusions. Are cybersecurity professionals guilty of ‘survivorship bias’ when it comes to security reinforcements after breaches and attacks? The answer is very likely “Yes,” and this logic error could be resulting in a much higher rate of data breach recurrence due to misplaced attention on the wrong security areas. Let’s dive a little deeper.
What Does Survivorship Bias Have to Do with Data Security?
When information security, IT, and data professionals look at past breaches to ensure a similar attack doesn’t happen again, they tend to focus on the proverbial “bullet holes in the returning planes;” that is, the gaps that enabled cyber threat actors to breach their systems. This often means focusing primarily on:
- Identities: Who/what served as the door to allow the threat actor to breach the system.
- Perimeter Security: Where are the gaps in the perimeter security and what needs to be done to secure those areas?
The immediate and natural instinct is to reinforce these identity and perimeter gaps and holes. And this typically means expanded identity and access management (IAM) security solutions, adding a few firewalls, and perhaps installing an intrusion detection system (IDS).
But as most cyber, IT, InfoSec, and data professionals know, no IAM or perimeter security system is foolproof. They’re necessary, to be sure, but are they really solving the complete security problem? When the cyber threat actor attacks your systems, is his end goal to bring down your entire IAM solution? No, probably not. The end goal is to bring down all your sensitive data. So the question then becomes, in the ongoing dogfights between cyber threat actors and an organization’s own ace fighter pilots—aka cybersecurity professionals—why is the focus not on data security?



Modern Data Security Is More than Identities and Perimeters
When reinforcing cybersecurity systems, security solutions need to go beyond just identities and the perimeter; they need to extend their focus to a cyber threat actor’s primary attack goal—the data—with a data security solution that answers three key questions:



Most businesses protect their sensitive data by focusing on security from the “outside in;” that is the perimeters and identities, looking at gaps and what those identities have access to. The problem with this approach is that data stores, and who or what have access to them, are too complex for any company to manage. Further, no IAM or perimeter solution is going to be able to provide the level of reinforcement necessary to completely protect the data.
A Data Security Posture Management (DSPM) solution shifts the survivorship bias from just identities and perimeters to extend the Zero Trust philosophy to hybrid-cloud data stores by securing organizations beginning with the data or “inside out,” instead of beginning with the perimeter or “outside in.”
DSPM helps organizations:
- Understand where sensitive data is located.
- Reduce data sprawl.
- Inform and control least privilege IAM permissions.
- Prioritize data security risks.
- Reduce data blast radius.
- Remediate data breach and attack impact.
- Manage insider threats and vendor, supplier, and third-party risk by providing insight into which identities have access to which data.
- Facilitate audit and compliance capabilities.
Data Security Posture Management (DSPM) Is the Answer to Cybersecurity Survivorship Bias
Businesses operate in a data-centric world, dominated by multi- and hybrid-cloud environments and data stored in a multitude of fragmented locations—from data stores and applications to third-party vendors and SaaS providers. There is a level of complexity to today’s business data that is, in a way, incomprehensible—millions of data objects across thousands of data stores, multiplied by a seemingly infinite combination of roles and permissions for thousands of user and machine identities.
The question that businesses need to be asking is how focusing solely on the perimeter and the identities is going to improve cybersecurity, when, in fact, most businesses are already struggling properly inventory, classify, control, and secure their critical data assets, while at the same time securing this data from attacks, insider threats, third-party supply chain attacks, vendor threats, and data breaches. Government regulations and industry mandates further complicate the data security process.
Data security posture management or DSPM addresses the cybersecurity survivorship bias.
DPSM solutions focus on protecting from what we like to call the “four horsemen of data breaches”— unauthorized access, regulatory and mandate non-compliance, data alteration, and data destruction by assessing data stores and flows, offering data classification and data mapping, and most importantly, working together with IAM and perimeter solutions to identify indicators of compromise (IOCs), understand data residency, and alert to vulnerabilities, exposures, misconfigurations, and improper cross-border data transfer,.
In the true vision of mathematician Abraham Wald, it’s this resulting information that removes the cybersecurity survivorship bias and provides the best visibility and insight into an organization’s data risk posture by enabling organizations to surface sensitive, dormant, and over-privileged data objects and anomalous data flows.
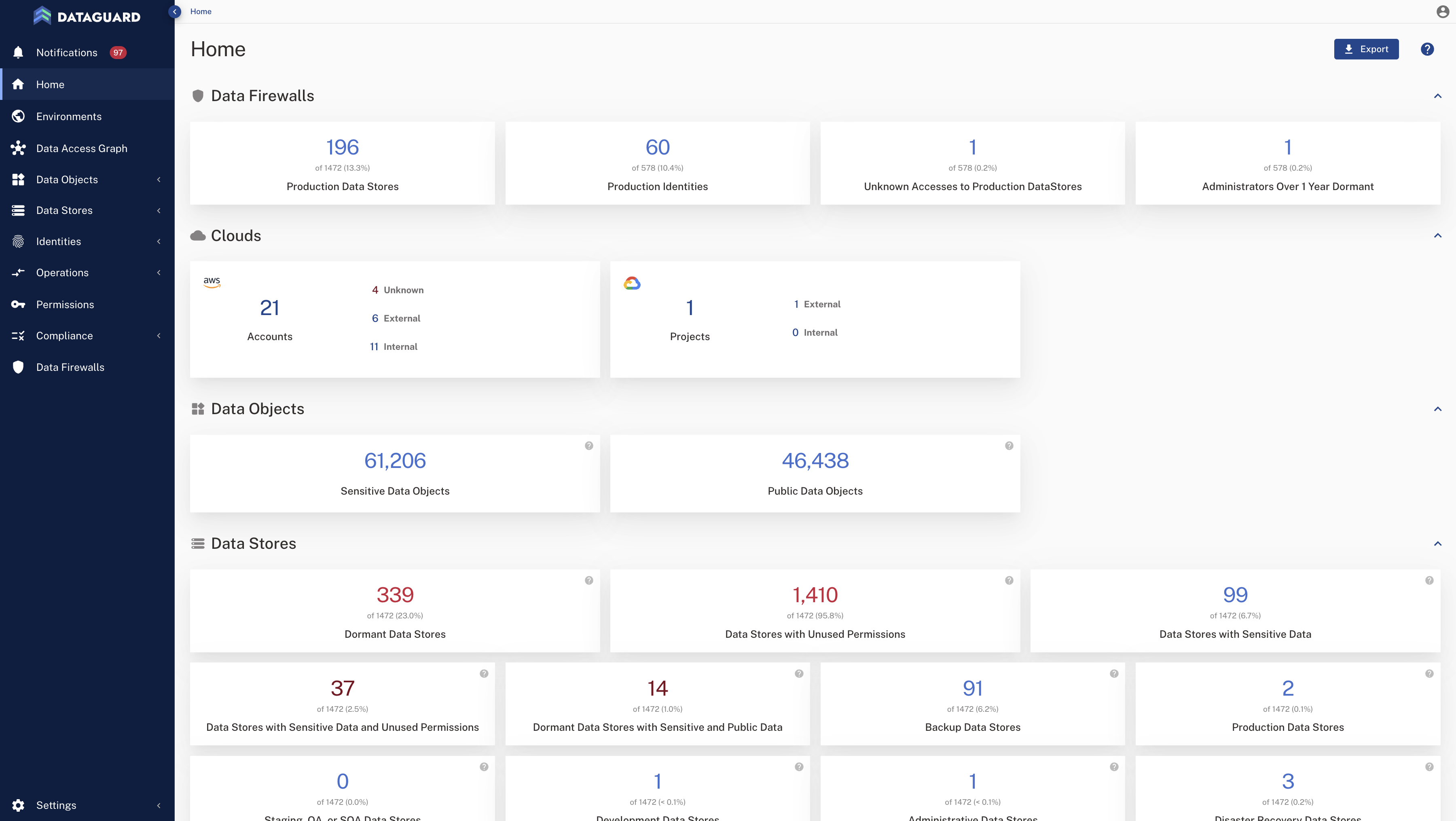


Data Security Posture Management (DSPM) surfaces issues like sensitive, dormant, and over-privileged data objects.
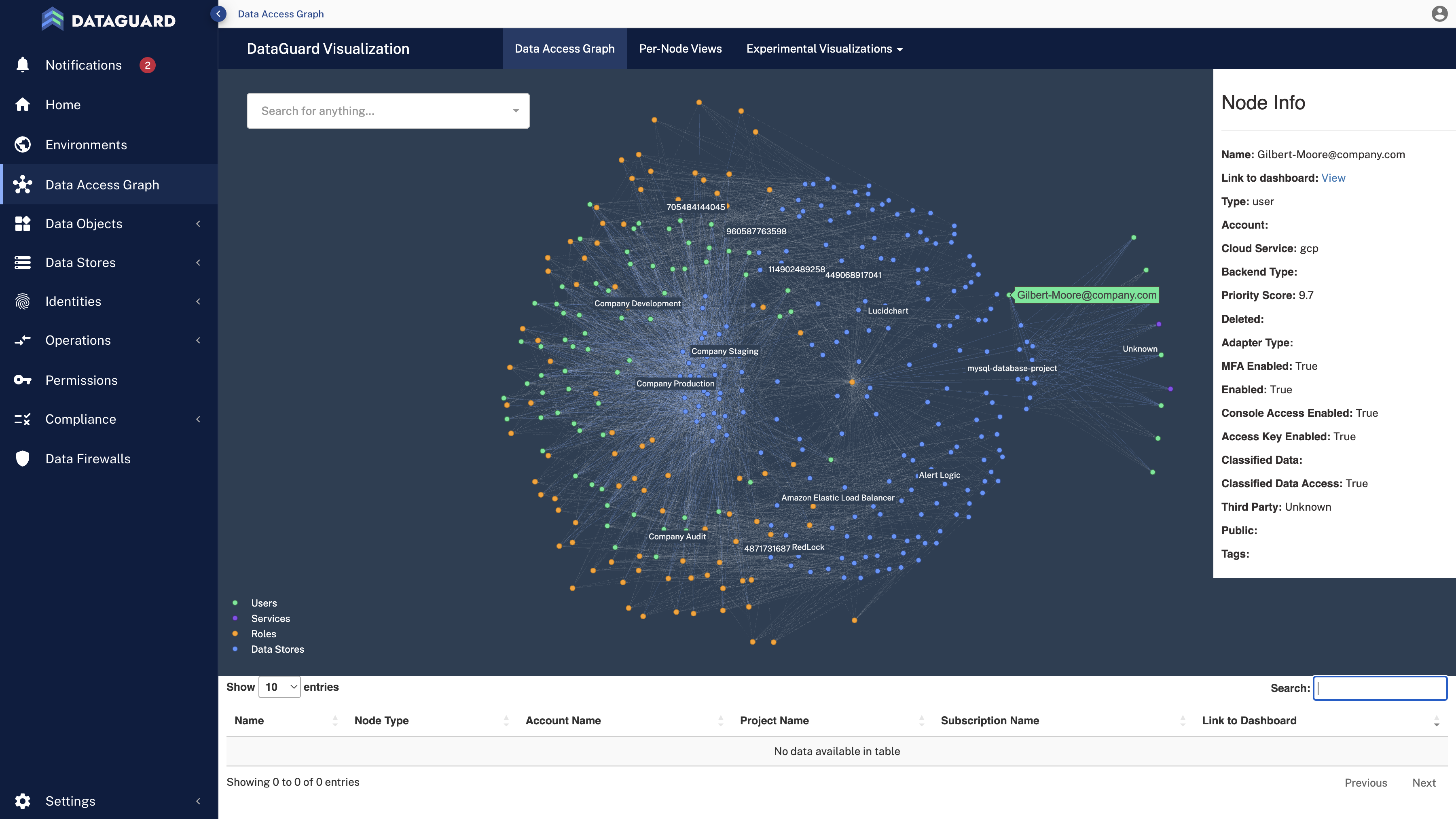


Data Security Posture Management (DSPM) solutions map how data flows within and outside an organization, offering total visibility and insight into an organization’s data risk posture.
Key DSPM capabilities include:
- Visualizing and securing data and data flow across environments.
- Managing compliance and privacy at the data object level.
- Reducing the data blast radius from insider threats, vendors, and third parties.
- Anomalous data behavior monitoring and alerting.
- Leading with effective data breach investigation and response.
Stop Cybersecurity Survivorship Bias
It’s time to stop chasing threats at only the perimeter and identity level. Securing mission-critical data at precision and scale means knowing your data security posture.
To learn more about data security posture management, let us show you our demo, which can help you better understand how to implement controls that prevent cybersecurity survivorship bias and protect from data incidents, breaches, and attacks.














