The California Privacy Rights Act (CPRA) (also sometimes called Proposition 24) went into effect on January 1, 2023. Approved by the majority of California voters in 2020, the CPRA expands and builds upon the privacy protections found in the California Consumer Privacy Act (CCPA) of 2019. While most organizations have already taken measures to be in compliance with the CCPA, which went live on January 1, 2020, some may not be aware that new personally identifiable information (PII) protection controls have been added as part of CPRA.
Major Differences Between CPRA and CCPA
The CPRA adds more provisions to California state law to protect consumers and give them the power to prevent businesses from sharing their data. It also enables consumers to correct inaccuracies and limits business use of “sensitive personal information” (SPI), such as race, religion, ethnicity, genetic data, geolocation, sexual orientation, certain types of health information, and private communications. Additionally, the CPRA creates an entity called the California Privacy Protection Agency (CPPA) dedicated to implementing and enforcing state privacy laws, investigating violations, and assessing violation penalties. Of particular note for cybersecurity professionals and organizations holding personal data, the CPRA also authorizes the use of civil penalties for the theft of specific login information. Some highlights of the differences between the original CCPA and updated CPRA include:
- Increases the consumer data limit from 50,000 to 100,000 for regulatory scope.
- Places the sharing of PII information in regulatory scope. (Previously only selling was regulated.)
- Introduces Sensitive Personal Information (SPI) as a new category of data that requires additional technical and operational control.
- Includes additional consumer rights.
- Mandates higher controls for data collection, usage, and retention.
- Expands protection to consumer login credentials.
- Establishes the California Privacy Protection Agency (CPPA).
CCPA and CPRA History and Background
California is among the states at the forefront of consumer rights protection regulations. California legislators drafted and approved the first version of the privacy regulation—known as CCPA—in 2019. CCPA went into effect in 2020. CPRA is the latest version of CCPA, and while it does not replace CCPA, it does serve as an amendment to the original legislation.
- GDPR: May 25, 2018
- CCPA: January 1, 2020
- CPRA: January 1, 2023
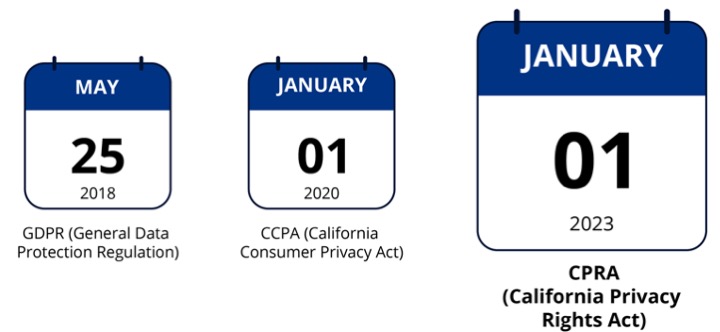
The California Privacy Rights Act (CPRA) went into effect on January 1, 2023.
CPRA Core Elements
The core elements of CPRA serve to establish the following protections for consumers:
- The right to know who is collecting their personal information and that of their children, how it is being used, and to whom it is disclosed.
- Control the use of their personal information, limit the use of sensitive personal information, and have meaningful options over how it is collected, used, and disclosed.
- Have access to their personal information and with the ability to correct it, delete it, and take it with them from one business to another.
- Be able to exercise these options through easily accessible self-serve tools.
- Be able to exercise these rights without being penalized for doing so.
- Be able to hold businesses accountable for failing to take reasonable precautions to protect their most sensitive personal information from hackers and security breaches.
- Benefit from businesses’ use of their personal information.
- Protect the privacy interests of employees and independent contractors.
Entities required to comply with CPRA are businesses that:
- Collect consumers’ personal information (on their own or by other businesses on their behalf).
- Does business in California.
- Satisfies at least one of the following thresholds:
- Has annual gross revenues in excess of $25 million.
- Alone or in combination, annually buys, receives, sells, or shares the personal information of 100,000 or more consumers, households, or devices.
- Derives 50% or more of its annual revenues from selling consumers’ personal information.
Let’s Talk “Sensitive Personal Information”
One of the key components of CPRA is the newly defined subset of personal information, known as “sensitive personal information” or SPI. The CPRA defines SPI as:
- Data found in social security, driver’s license, state identification card, or passport number.
- Login credentials (e.g., username and password).
- Financial information, including account information, debit card, or credit card number in combination with any required security or access code, password, or credentials allowing access to an account.
- Precise geolocation.
- Racial or ethnic origin, religious or philosophical beliefs, or union membership.
- Personal communications such as mail, email, and text messages
- Genetic data.
From a cybersecurity perspective, in addition to honoring the various consumer data rights, businesses also need to implement security safeguards. Specifically, CPRA requires:
“A business that collects a consumer’s personal information shall implement reasonable security procedures and practices appropriate to the nature of the personal information to protect the personal information from unauthorized or illegal access, destruction, use, modification, or disclosure in accordance with Section 1798.81.5.”
Notably, however, the CPRA does not prescribe the specific safeguarding actions a business must take, such as the degree of encryption, the number of security systems, or the types of security technologies.
With that said, at the core of security is identity and access management and having complete visibility into:

Having comprehensive and coherent visibility into your entire data landscape, including a complete risk map, is critical to managing CPRA (as well as GDPR and others). A new Gartner-defined solution, known as Data Security Posture Management (DSPM), “provides visibility as to where sensitive data is, who has access to that data, how it has been used and what the security posture of the data store or application is.” From a data privacy perspective, DSPM is key to security and data privacy as it:
- Assists businesses in understanding where sensitive data is located.
- Removes ‘dormant data’ (i.e., data no longer in use), reducing the risk of exposure.
- Highlights sources of PII and SPI to improve the security audit process or identify high risk applications.
- Offers timely and meaningful alerts into data breaches and unusual or malicious activity.
- Reduces in the data blast radius.
- Offers data breach and attack remediation.
- Facilitates audit and compliance capabilities.
The Importance of Privacy Program Management
Before we discuss technical aspects of DSPM and personal data protection, let us quickly review the key elements of privacy program management. Below are the important steps of privacy program management.
- Document the required personal data that to be collected and how it will be used.
- Communicate to consumers.
- Get consent from the consumers where required.
- Define resources, roles, and responsibilities for data protection and governance.
- Store and process the data.
- Implement data lifecycle including retention and purge.
- Perform periodic data impact analysis.
- Implement privacy data operations that will receive and address data subject rights requests.
- Periodically monitor for regulations updates and new regulations and align the privacy program.
DSPM Solutions that Support Compliance
The common and important element of the above tasks is identifying and governing data assets that hold personal data. For privacy professionals, Symmetry Systems’ DPSM solution, DataGuard, is designed solely to protect data from different threats and also help customers meet stringent data protection regulations. DataGuard provides many key compliance functionalities, including:
- A list of cloud data assets and any PII in those assets.
- A list and visual information about users and roles that have access to PII data.
- Diagrams that visually depict data transfer flow between systems.
- Location transparency and transfer across regions.
- Activities performed by identities and systems on PII data.
- Platform for organizations to build their own custom PII classifiers.
- Comprehensive set of security and compliance rules out of box for smarter data governance.
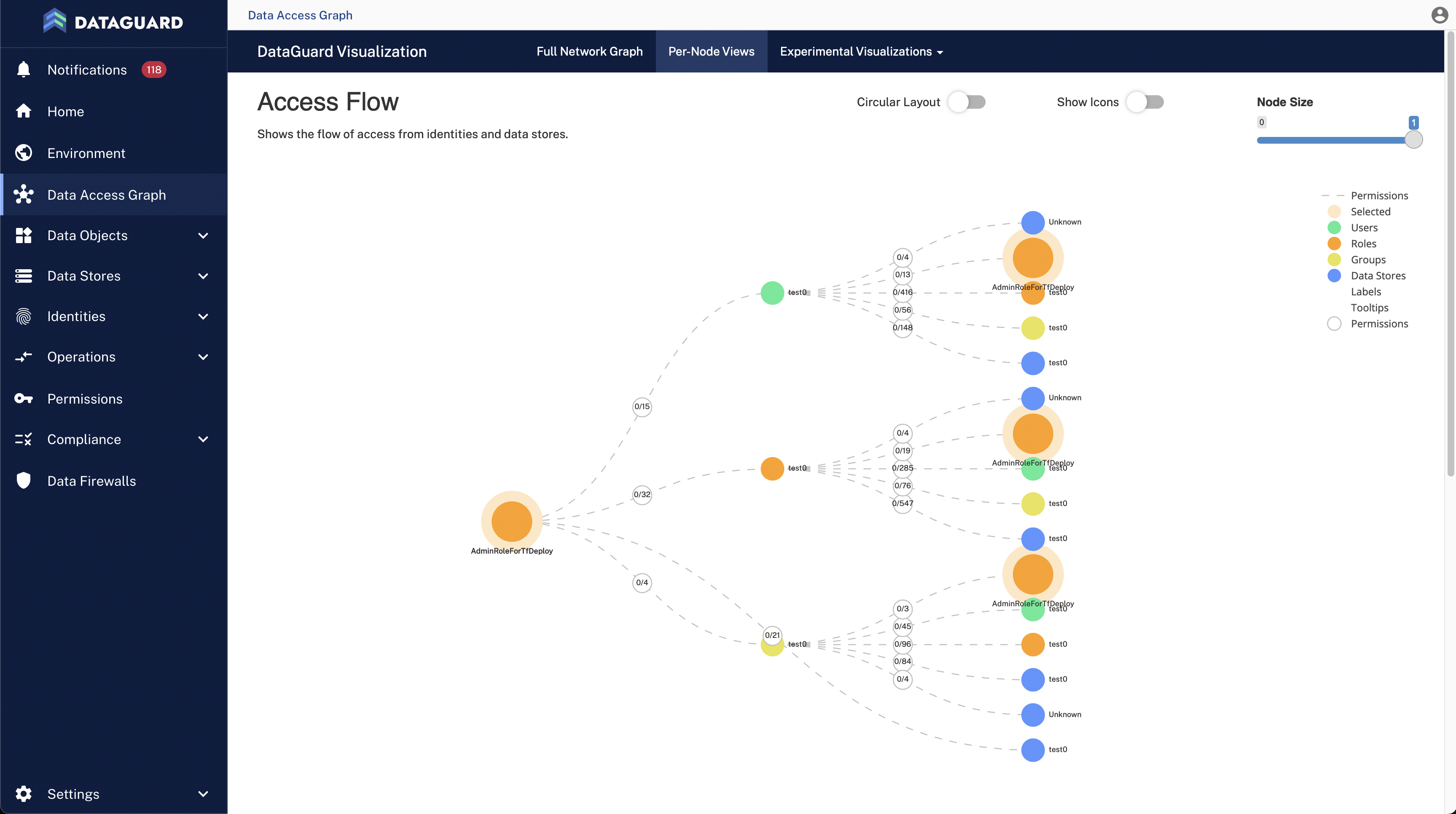
Data Security Posture Management (DSPM) solutions, like DataGuard, offer data visualizations that provide actionable insights.
Learn More
As most of the organizations grow, the systems and data in scope for CPRA compliance also grow in size and complexity. To be on top of privacy regulations that heavily focus on protecting data, organizations need to rely on data-centric cybersecurity and privacy platforms. Symmetry Systems’ DSPM solution, DataGuard, is built with features for PII data governance. The Symmetry team is here to help you to make your CPRA compliance journey easier.






