Zero-Trust Assessments
Let Symmetry Systems Help You Enforce Data Security
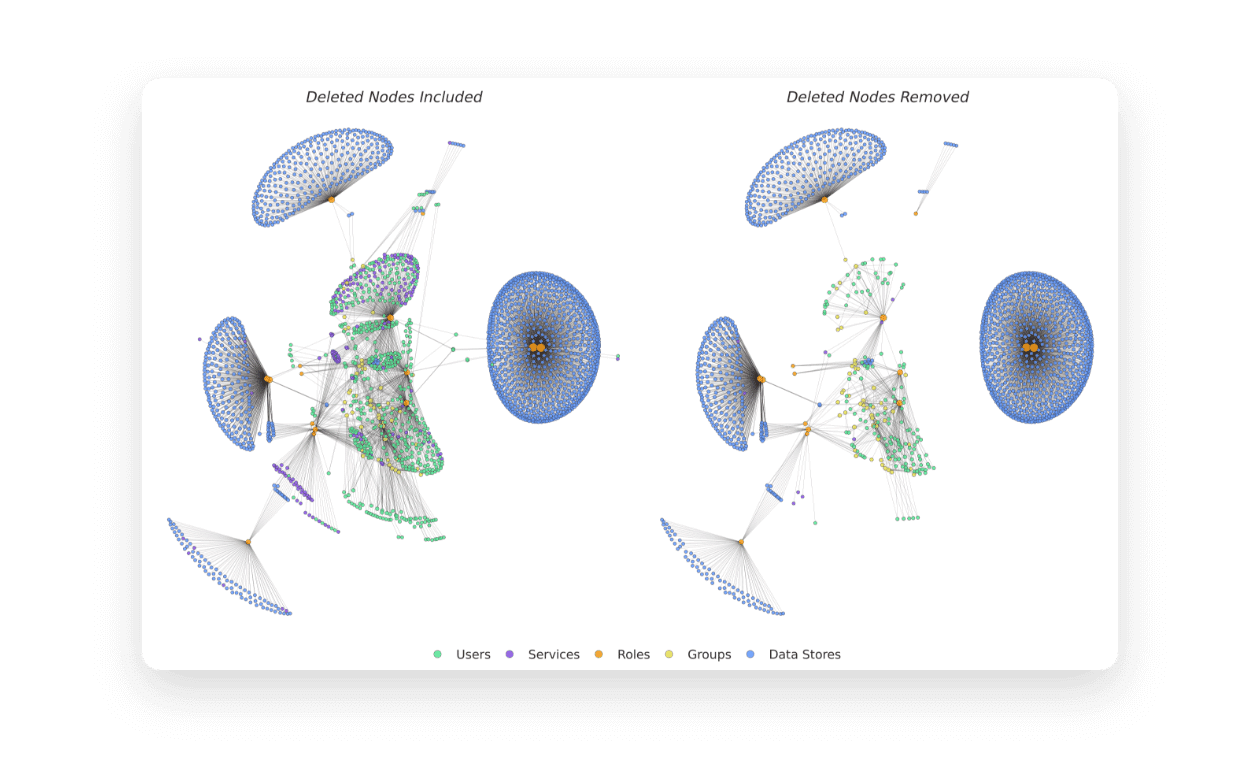
More and more, organizations are turning toward “Zero Trust” as a way to secure their organizations. They implement “Zero-Trust technologies”, build “Zero-Trust Architectures”, and go to bed at night believing their data has been secured. But without performing a deep assessment on the data itself, how do they know?
Zero-Trust Data Assessments from Symmetry Systems help organizations develop an accurate understanding of their data—from types of data and sensitivity of data objects, their locations, who and what is entitled to access the data, how it is secured, and in what manner it has been accessed. Only with deep insights into their data security posture can organizations properly follow the Zero-Trust philosophy to protect their users, their data, and their ability to grow their businesses securely.