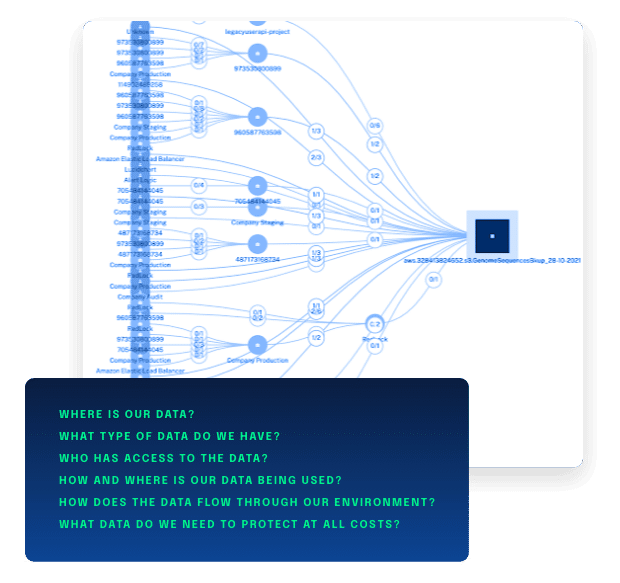
Data Inventory and Data Flow Mapping
Visualize Data Inventory and Data Flows, Not just Boxes and Clouds
Accurate visibility is an essential component of organizational cybersecurity, especially as annual data compromise numbers continue to climb. Many organizations spend countless resources on tools and cloud technologies to build “Zero-Trust architectures” around their data, without putting any focus on the security of their data.
DataGuard takes an data-out approach to helping organizations understand their data, by visualizing the inventory and flows across your on-prem and hybrid clouds, of the most important part of your architecture—the data itself.