Data Detection and Response
Quickly Answer The Most Burning Data Questions During a Security Incident
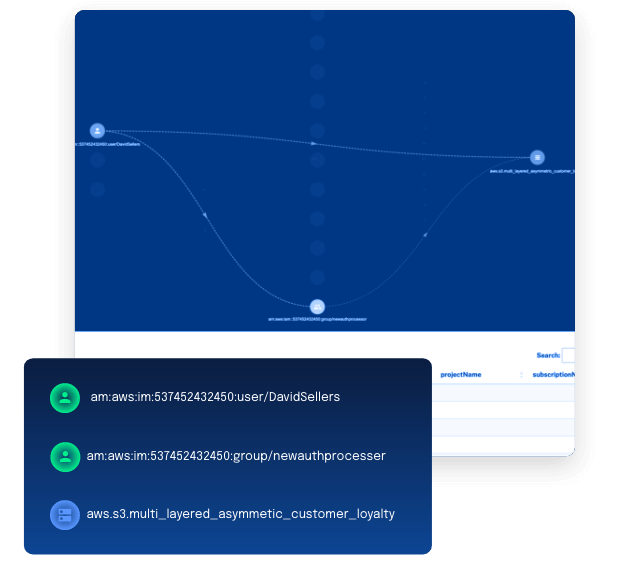
Security operations, forensics, and incident response teams need fast answers for two basic questions when responding to or investigating an incident: has any data been accessed and by who?
Historically, getting that answer relied on specialist digital forensic and incident response providers who could take weeks to forensically comb through logs using a combination of forensic tools and deep cybersecurity expertise to piece together what happened down to the individual data objects. This can bog down response while precious moments tick away that allows attackers to do more damage.